Install OpenSSL on Windows 10/11: A Step-by-Step Guide
Historically, utilizing OpenSSL necessitated either operating within a Linux environment or engaging in the manual compilation of its source code for both Mac and Windows users. However, with the advent of Win32/Win64 OpenSSL, this powerful open-source cryptography library has been made accessible to users of both 32-bit and 64-bit Windows operating systems, allowing for seamless integration into Windows environments through a straightforward installation process.OpenSSL is renowned for its pivotal role in securing data across a myriad of applications and network connections. It is instrumental in encrypting data for SSL/TLS protocols, thereby ensuring secure HTTPS connections, and is also utilized in the encryption processes for SSH, OpenVPN, and DNSSEC, among others.Thanks to the efforts of Shining Light Productions, the deployment of OpenSSL on Windows has been significantly simplified. The Win32/Win64 OpenSSL Installation Project, available at slproweb.com, offers an installer that streamlines the process, bypassing the complexity of manual compilation by providing ready-to-use binaries. This development not only facilitates easier access to OpenSSL’s robust security features but also enhances the security infrastructure of Windows-based systems with minimal effort. The OpenSSL package is now installed. The second method is to download and install the package.
The OpenSSL package is now installed. The second method is to download and install the package. Initiate the Installation Process: Search for the “Win64 OpenSSL v3.0.7 EXE Light” option, which should be prominently displayed at the top of the list. Download this file and, once the download is complete, navigate to your download directory and double-click the Win64OpenSSL_Light-3_0_7.exe file to start the setup process.
Initiate the Installation Process: Search for the “Win64 OpenSSL v3.0.7 EXE Light” option, which should be prominently displayed at the top of the list. Download this file and, once the download is complete, navigate to your download directory and double-click the Win64OpenSSL_Light-3_0_7.exe file to start the setup process. Navigate the Setup Wizard: Upon launching the installer, you may encounter a User Account Control (UAC) prompt. Click
Navigate the Setup Wizard: Upon launching the installer, you may encounter a User Account Control (UAC) prompt. Click 
 Navigate to Environment Variables: In the System Properties window that appears,
Navigate to Environment Variables: In the System Properties window that appears, locate and click on the ‘Environment Variables’ button situated at the lower section of the window.
locate and click on the ‘Environment Variables’ button situated at the lower section of the window. Modify the System Path: Within the Environment Variables window, scroll to find the ‘Path’ variable under the ‘System Variables’ section. Select it and then click the ‘Edit’ button. This action opens the ‘Edit Environment Variable’ window, where you will add the path to the OpenSSL installation.
Modify the System Path: Within the Environment Variables window, scroll to find the ‘Path’ variable under the ‘System Variables’ section. Select it and then click the ‘Edit’ button. This action opens the ‘Edit Environment Variable’ window, where you will add the path to the OpenSSL installation.
 Specifically, you’re aiming to include the path to the OpenSSL-Win64\bin directory, which is typically located within the Program Files directory. This path houses the openssl.exe executable. Utilize the Browse button or directly paste the path if you have it ready. Confirm by clicking OK.Add OPENSSL_CONF Variable: For OpenSSL to function correctly, it needs to know where to find its configuration file. Achieve this by adding a new system variable. Click ‘New’ within the System Variables section and enter OPENSSL_CONF as the variable name. In the variable value field, input the path to your openssl.cnf file, which is usually located at
Specifically, you’re aiming to include the path to the OpenSSL-Win64\bin directory, which is typically located within the Program Files directory. This path houses the openssl.exe executable. Utilize the Browse button or directly paste the path if you have it ready. Confirm by clicking OK.Add OPENSSL_CONF Variable: For OpenSSL to function correctly, it needs to know where to find its configuration file. Achieve this by adding a new system variable. Click ‘New’ within the System Variables section and enter OPENSSL_CONF as the variable name. In the variable value field, input the path to your openssl.cnf file, which is usually located at 
Comprehensive Guide to Setting Up OpenSSL on Windows
Deploying OpenSSL on Windows 10 and Windows 11 has become more accessible, and this guide outlines two straightforward methods for installation. Begin with the most direct approach by leveraging the Windows Package Manager. To initiate this process, press the Windows-logo+R keys simultaneously to open the ‘Run’ dialogue box, type ‘cmd’, and select OK. Alternatively, you can press the Windows key, search for ‘cmd’, and then select the command prompt icon from the search results.Once you open the command prompt window, enter the following command to install OpenSSL. If your user account doesn’t have administrative privileges, right-click on the command prompt and choose “Run as administrator” for elevated access.<“C:\> winget install openssl”>The command line tool ‘winget’ serves as a versatile package manager for Windows, simplifying the installation of software applications and packages directly from the command line interface. When you run 'winget‘ for the first time, it may ask you to accept the terms of the source agreement. You can do this by pressing the ‘Y’ key when prompted.
This method showcases the simplicity and efficiency of using 'winget' for software installations on Windows platforms, streamlining the process of getting OpenSSL up and running on your system without the need for intricate steps or manual downloads.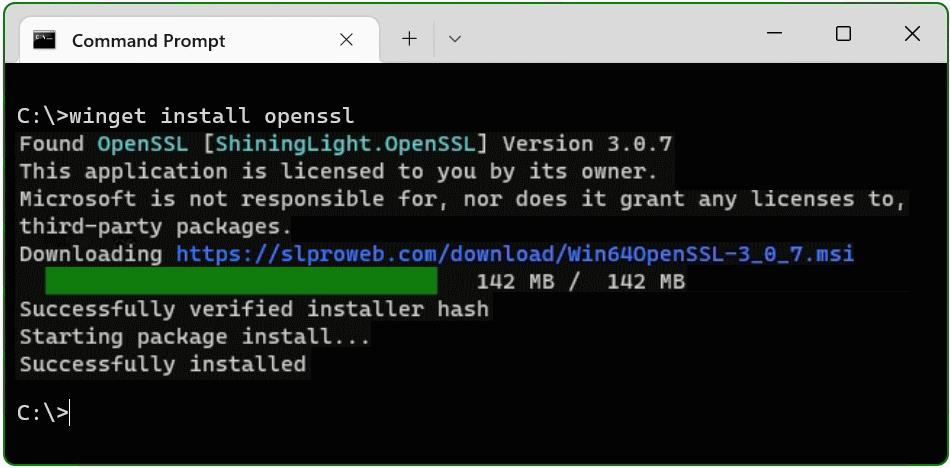 The OpenSSL package is now installed. The second method is to download and install the package.
The OpenSSL package is now installed. The second method is to download and install the package.Step-by-Step Guide to Downloading and Installing Win64 OpenSSL
Locate the Installer: Visit the official Shining Light Productions website at https://slproweb.com/products/Win32OpenSSL.html to find the installer. It’s advisable to opt for the most recent version to ensure you have the latest security and functionality enhancements. As of the last update to this guide, the Win64 OpenSSL v3.0.7 EXE Light version is recommended for its balance of features and lightweight installation.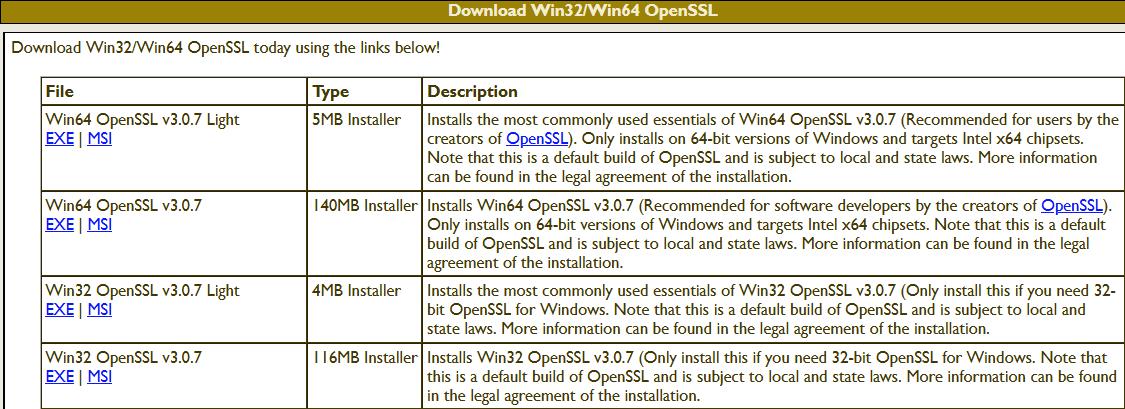 Initiate the Installation Process: Search for the “Win64 OpenSSL v3.0.7 EXE Light” option, which should be prominently displayed at the top of the list. Download this file and, once the download is complete, navigate to your download directory and double-click the Win64OpenSSL_Light-3_0_7.exe file to start the setup process.
Initiate the Installation Process: Search for the “Win64 OpenSSL v3.0.7 EXE Light” option, which should be prominently displayed at the top of the list. Download this file and, once the download is complete, navigate to your download directory and double-click the Win64OpenSSL_Light-3_0_7.exe file to start the setup process.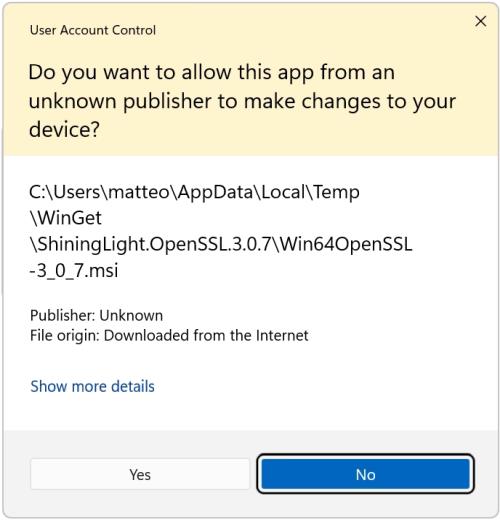 Navigate the Setup Wizard: Upon launching the installer, you may encounter a User Account Control (UAC) prompt. Click
Navigate the Setup Wizard: Upon launching the installer, you may encounter a User Account Control (UAC) prompt. Click 'Yes' to affirm your decision to proceed with the installation. This action will activate the setup wizard, which will guide you through the necessary steps to successfully install OpenSSL on your Windows system. The wizard automates the process of unpacking and transferring the necessary OpenSSL files to their designated locations on your computer.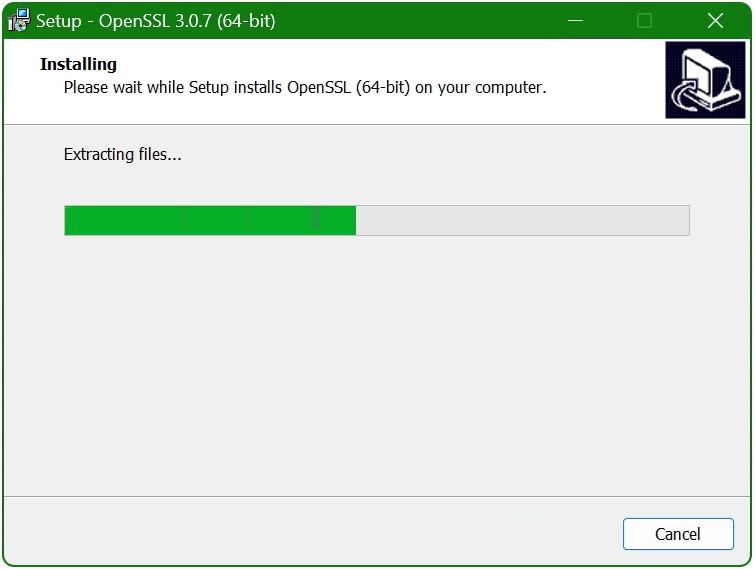
Integrating OpenSSL into the Windows Environment
Access System Properties: Begin by opening the Run dialog box using the Windows + R shortcut, then type SYSTEM PROPERTIES ADVANCED and click OK to proceed.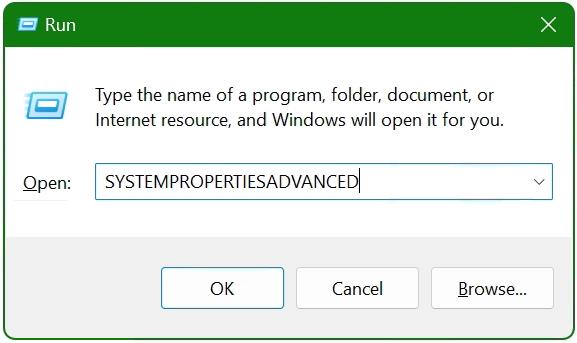 Navigate to Environment Variables: In the System Properties window that appears,
Navigate to Environment Variables: In the System Properties window that appears,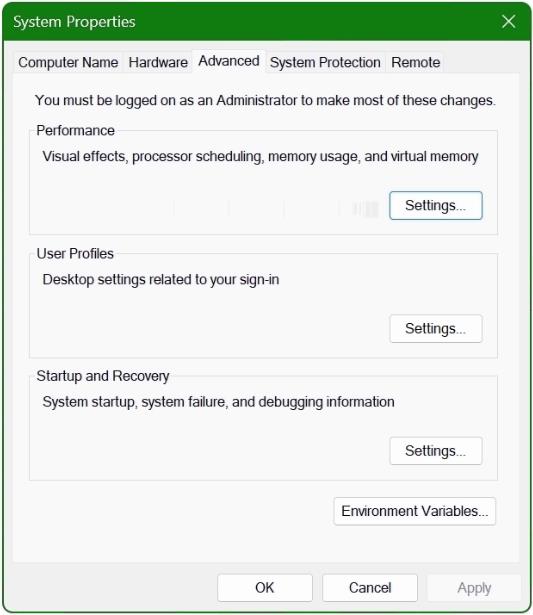 locate and click on the ‘Environment Variables’ button situated at the lower section of the window.
locate and click on the ‘Environment Variables’ button situated at the lower section of the window.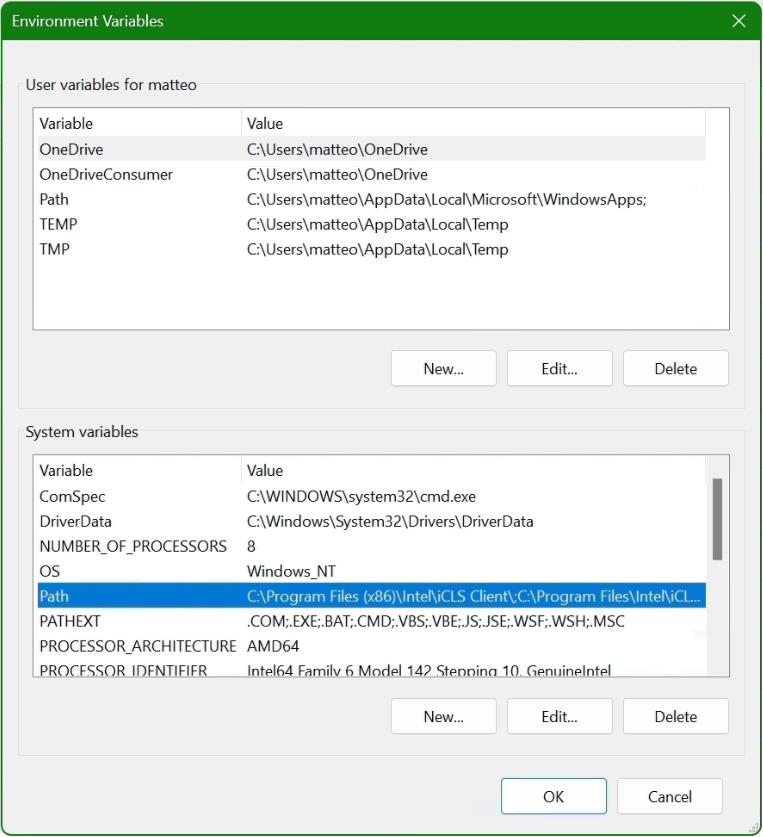 Modify the System Path: Within the Environment Variables window, scroll to find the ‘Path’ variable under the ‘System Variables’ section. Select it and then click the ‘Edit’ button. This action opens the ‘Edit Environment Variable’ window, where you will add the path to the OpenSSL installation.
Modify the System Path: Within the Environment Variables window, scroll to find the ‘Path’ variable under the ‘System Variables’ section. Select it and then click the ‘Edit’ button. This action opens the ‘Edit Environment Variable’ window, where you will add the path to the OpenSSL installation.
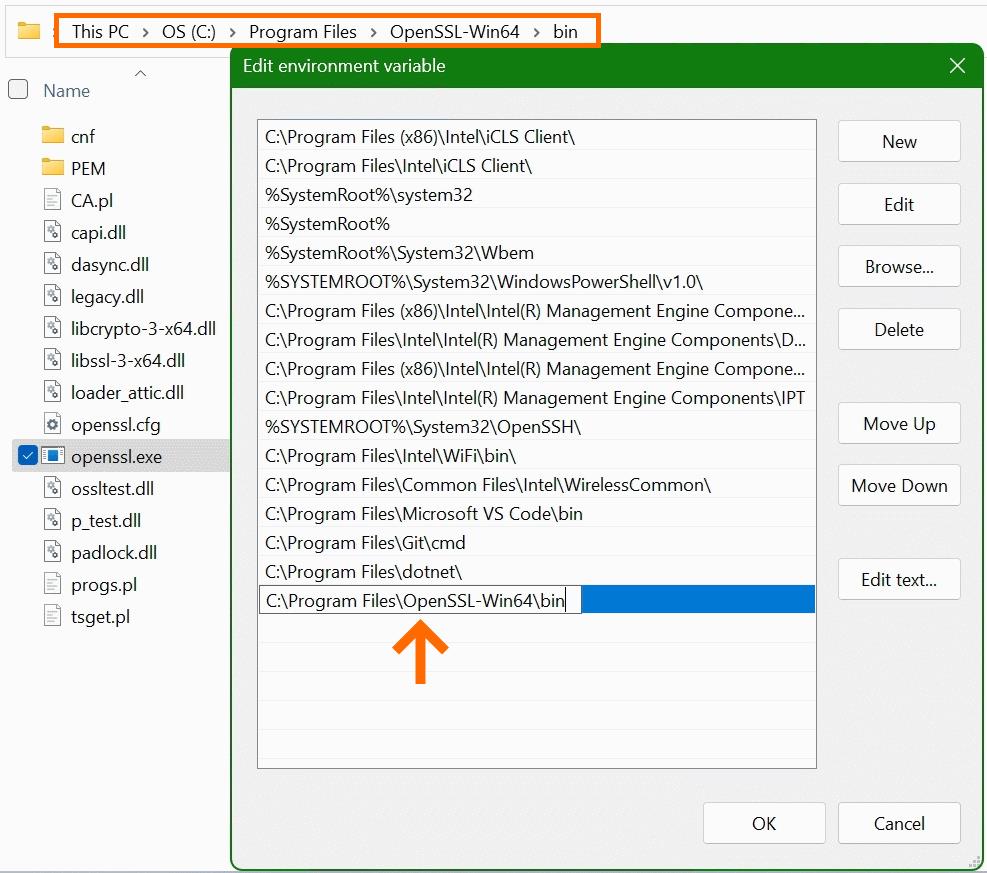 Specifically, you’re aiming to include the path to the OpenSSL-Win64\bin directory, which is typically located within the Program Files directory. This path houses the openssl.exe executable. Utilize the Browse button or directly paste the path if you have it ready. Confirm by clicking OK.Add OPENSSL_CONF Variable: For OpenSSL to function correctly, it needs to know where to find its configuration file. Achieve this by adding a new system variable. Click ‘New’ within the System Variables section and enter OPENSSL_CONF as the variable name. In the variable value field, input the path to your openssl.cnf file, which is usually located at
Specifically, you’re aiming to include the path to the OpenSSL-Win64\bin directory, which is typically located within the Program Files directory. This path houses the openssl.exe executable. Utilize the Browse button or directly paste the path if you have it ready. Confirm by clicking OK.Add OPENSSL_CONF Variable: For OpenSSL to function correctly, it needs to know where to find its configuration file. Achieve this by adding a new system variable. Click ‘New’ within the System Variables section and enter OPENSSL_CONF as the variable name. In the variable value field, input the path to your openssl.cnf file, which is usually located at C:\Program Files\OpenSSL-Win64\bin\cnf\openssl.cnf. Confirm all actions by clicking OK.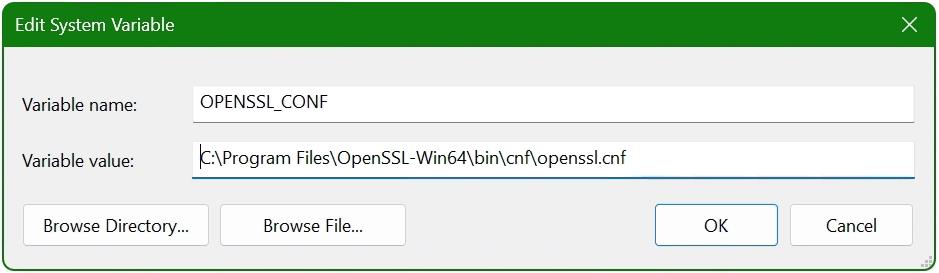
Verifying the Installation
To confirm that OpenSSL has been correctly set up and is operational, open a command prompt window and execute the following commands:To check the version and build information of your OpenSSL installation, enter:“C:\> openssl version -a”This command will display details such as the version number and build date.To ascertain the directory where OpenSSL searches for its configuration files, use:“C:\> openssl version -d”This returns the OPENSSLDIR path, indicating where the OpenSSL configuration files reside.Utilizing OpenSSL on WindowsWhile Windows does not support the ‘man’ pages common on Linux for detailed command documentation, OpenSSL on Windows provides a helpful alternative. The openssl help command offers context-sensitive guidance for using its various functions. For example, you can use openssl help s_client, openssl help x509, or openssl help req to get specific information on these commands. Additionally, extensive documentation and manual pages are available online, offering a wealth of information to both new and experienced users.Mastering OpenSSL: Key Commands and Operations
OpenSSL is an incredibly robust toolkit that offers an array of functionalities for managing and manipulating SSL/TLS certificates, keys, and other cryptographic tasks. Below, we explore several essential OpenSSL commands that are widely used for security and certificate management. This list is not exhaustive but highlights some practical examples of how OpenSSL can be utilized effectively.Essential OpenSSL Commands for Security Experts
– Inspecting Certificate Details: To examine the details of a certificate file named `ca-cert.pem` without altering its content, use the following command:openssl x509 -noout -text -in ca-cert.pemThis command outputs the certificate’s details in a readable format, making it easier to review its contents.– Verifying Certificate Signing Requests (CSRs): For scrutinizing and confirming the data within a CSR file named `x509-check.csr`, execute:openssl req -text -noout -verify -in x509-check.csrThis ensures the integrity and correctness of the CSR’s information.– Checking Key File Integrity: To verify the structural integrity of a key file, such as `rootCA.key`, use:openssl rsa -check -in rootCA.keyThis command helps ensure that the key file is valid and has not been corrupted.– Computing Certificate Checksum: To calculate the MD5 checksum of a certificate file `ca-cert.pem`, facilitating the verification of its integrity, perform:openssl x509 -noout -modulus -in ca-cert.pem | openssl md5– Converting Certificate Formats: To transform a PEM format certificate `servercert.pem` into a PKCS#7 format and save it as `servercert.p7b` in a temporary directory, execute:openssl crl2pkcs7 -nocrl -certfile servercert.pem -out c:\temp\servercert.p7b– Exporting to PKCS#12 Format: To convert a certificate `rootCA.pem` and its key `rootCA.key` into a PKCS#12 format file named `rootCA.p12`, use:openssl pkcs12 -export -in rootCA.pem -inkey rootCA.key -out c:\temp\rootCA.p12 -name "PKCS12 certificate"– Generating SSL Certificates: For creating a new SSL certificate and key with RSA 2048 encryption and SHA256 hashing, valid for one year, the command is:openssl req -new -newkey rsa:2048 -sha256 -days 365 -nodes -x509 -keyout server.key -out server.crt– Testing Server Connections: To check the connection to an IMAP service on `imap.gmail.com` at port 993, use:openssl s_client -connect imap.gmail.com:993For SMTP with STARTTLS on `smtp.gmail.com` at port 587, the command is:openssl s_client -crlf -connect smtp.gmail.com:587 -starttls smtpAnd to verify the connection details of `www.ietf.org` at port 443 quietly and briefly:openssl s_client -verify_quiet -brief www.ietf.org:443– Generating Random Passwords: To create a secure random password in base64 format, which could be used to safeguard private keys, execute:openssl rand -base64 20These commands represent just a fraction of what OpenSSL can accomplish. Its versatility extends far beyond these examples, serving as a critical tool for anyone working with encryption, certificates, and secure communications.
4.6/5 - (5 votes)







