
Step-by-Step Guide: Installing and Configuring OpenVPN on Debian
Contents
OpenVPN is one of the most widely trusted VPN platforms in the world for building secure, encrypted tunnels between devices and networks. When deployed on a Debian server, it becomes a powerful solution for privacy, remote access, and secure communication. This comprehensive guide will show you exactly how to install and configure OpenVPN on Debian step-by-step, explain how it works, and help you troubleshoot common problems without needing a table.
This guide covers everything from basics to advanced configuration, so both beginners and experienced Linux users can follow along easily.
1. What is OpenVPN and Why Should You Use It on Debian?
OpenVPN is an open-source virtual private network solution that creates secure tunnels over the internet using TLS/SSL encryption. It protects your data from hackers, ISPs, and surveillance systems. Debian is one of the best Linux distributions for running OpenVPN because of its stability, security patches, and performance.
Key advantages of OpenVPN on Debian
- Strong AES-256 encryption
- Free and open-source
- Works behind NAT and firewalls
- Cross-platform compatibility
- Perfect for remote workers and servers
- Supports TLS authentication
- Excellent community support
What OpenVPN is commonly used for
- Secure remote employee access
- Hiding the real IP address
- Preventing ISP tracking
- Bypassing geo-blocking
- Connecting office branches
- Gaming security and latency control
- Secure IoT network connections
Debian is frequently deployed on VPS platforms such as DigitalOcean, AWS, Google Cloud, Hetzner, and on local servers, making it an ideal backbone for OpenVPN.
2. How to Install OpenVPN on Debian – Step-by-Step Tutorial
Follow the steps carefully in sequence.
Step 1: Update your Debian server
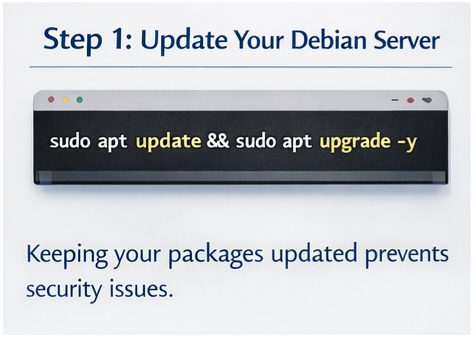
Keeping your packages updated prevents security issues:
sudo apt update && sudo apt upgrade -y
Step 2: Install OpenVPN and Easy-RSA
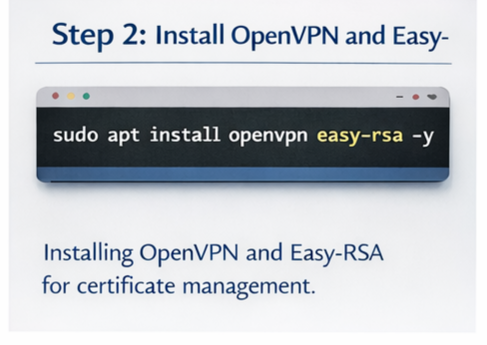
Easy-RSA helps generate encryption keys and certificates.
sudo apt install openvpn easy-rsa -y
Step 3: Create the Public Key Infrastructure (PKI)
make-cadir ~/openvpn-cacd ~/openvpn-ca
Initialize environment:
source vars./clean-all./build-ca
Step 4: Create the server certificate and key
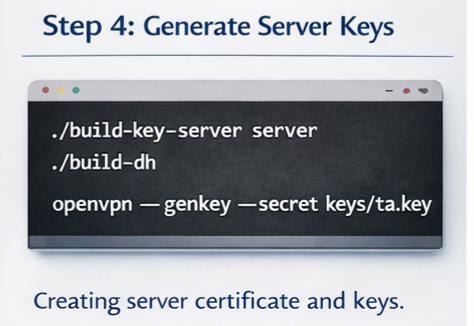
./build-key-server server./build-dhopenvpn --genkey --secret keys/ta.key
Step 5: Configure the OpenVPN server
Copy sample server configuration:
gunzip -c /usr/share/doc/openvpn/examples/sample-config-files/server.conf.gz | sudo tee /etc/openvpn/server.conf
Edit configuration:
sudo nano /etc/openvpn/server.conf
Important parameters to review:
- Port number (default 1194)
- Protocol (UDP recommended)
- Cipher method
- TLS authentication
- Keepalive settings
- DNS push settings
Step 6: Enable packet forwarding
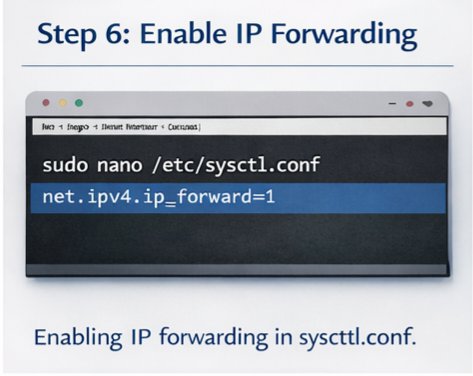
Open sysctl configuration:
sudo nano /etc/sysctl.conf
Uncomment:
net.ipv4.ip_forward=1
Apply the change:
sudo sysctl -p
Step 7: Configure firewall rules (UFW or iptables)
Allow OpenVPN traffic:
sudo ufw allow 1194/udp
Allow forwarding:
sudo ufw allow OpenSSHsudo ufw enable
For the iptables masquerading example:
sudo iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE
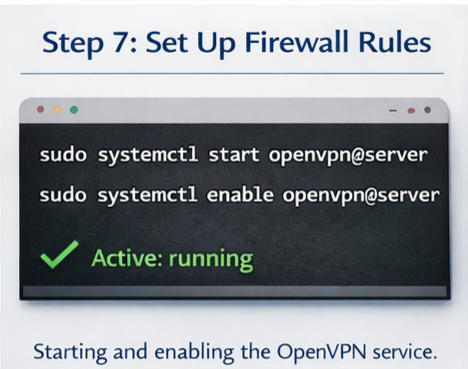
Step 8: Start and enable the OpenVPN service
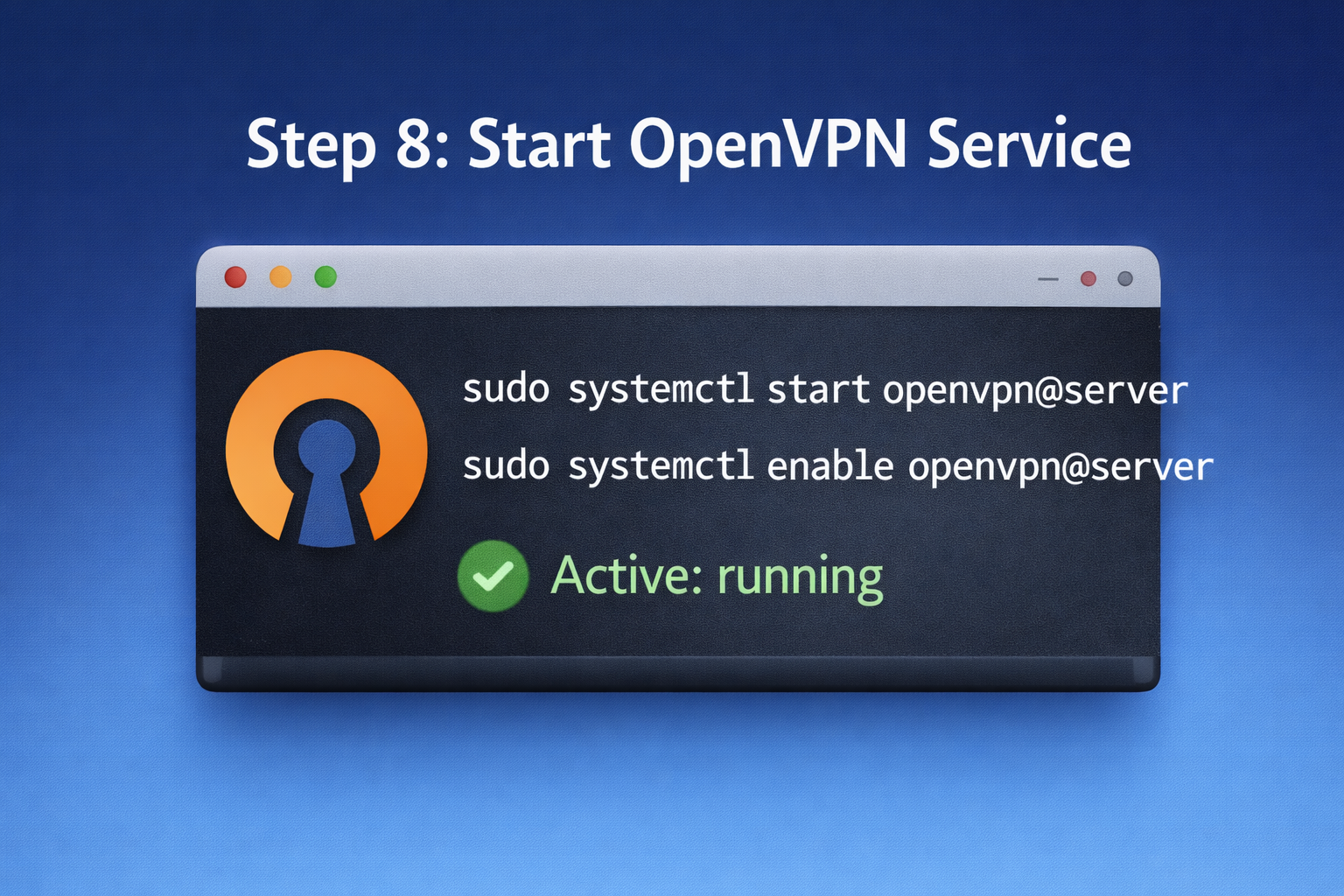
sudo systemctl start openvpn@serversudo systemctl enable openvpn@server
Check status:
sudo systemctl status openvpn@server
Your OpenVPN server is now ready.
3. How to Configure OpenVPN Client Files
Clients need:
- CA certificate
- Client certificate
- Client key
- key
- .ovpn configuration file
Export client profile:
./build-key client1
Create a combined client file structure for easy import on Windows/Android.
4. Common OpenVPN Problems and How to Fix Them (No Table Format)
Below are the most frequent errors and how to resolve them in plain text format.
❌ OpenVPN service does not start
➡️ Incorrect configuration or missing certificates
✔️ Solution: check logs
sudo journalctl -u openvpn@server --no-pager
❌ Client cannot connect to the server
➡️ Firewall blocking traffic
✔️ Solution: open UDP port 1194
❌ Connected but no internet
➡️ IP forwarding disabled
✔️ Solution: enable in sysctl, then reload
❌ TLS handshake failed
➡️ Authentication key mismatch
✔️ Solution: verify same ta. The key is used on both sides
❌ Connection is slow
➡️ Network congestion or wrong protocol
✔️ Solution: Try switching TCP/UDP or ports
❌ DNS leaks
➡️ Client not using VPN DNS
✔️ Solution: push DNS config in server.conf
❌ Frequent disconnections
➡️ Missing keepalive configuration
✔️ Solution: add keepalive 10 120
❌ No traffic passes
➡️ Missing NAT rules
✔️ Solution: configure iptables masquerade
❌ Permission denied
➡️ Not running as root
✔️ Solution: run OpenVPN using sudo
5. Best Practices for Optimizing OpenVPN on Debian
To improve security and performance:
- Use UDP whenever possible
- Change the default VPN port
- Use modern encryption suites
- Monitor logs regularly
- Rotate client certificates
- Use fail2ban for brute-force protection
- Keep Debian updated
- Disable weak ciphers
- Prefer AES-GCM over AES-CBC
- Avoid password-only authentication
Conclusion
Installing OpenVPN on Debian is one of the best ways to secure communications, protect privacy, and enable remote access to private networks. By carefully following the step-by-step instructions above, enabling IP forwarding, configuring firewall rules, and generating proper certificates, you can create a reliable and secure VPN environment.
With the troubleshooting guide and FAQs included, beginners can solve most issues without external help. Whether you’re using Debian for personal privacy, corporate security, or remote administration, OpenVPN remains one of the strongest, most flexible VPN solutions available today.

